Dark web websites: How to access them safely and where to find dark web links
The dark web is a hidden part of the internet that requires specific tools and knowledge to access securely. It hosts a variety of websites and services not available through standard search engines, often used for privacy-focused activities. To explore the dark web safely, it’s essential to use reputable onion browsers and follow best practices for digital security. Finding reliable dark web links can be challenging, but trusted directories and community recommendations can help you discover legitimate sources. For example, you might consider exploring links such as this darknet link to start your journey into deeper web exploration. Always prioritize safety and anonymity when accessing these sites to protect your identity and data.
Dark Web Websites: The Best Onion and Tor Links 2025

The dark web is a hidden part of the internet that requires special software to access, offering privacy and anonymity for its users. While it has legitimate uses, such as protecting privacy for journalists and activists, it can also host illegal activities. Navigating the dark web requires caution, proper tools, and awareness of safety measures to prevent potential dangers and security breaches. Understanding how to access dark web sites safely and where to find reliable links is essential for those interested in exploring this obscure part of the internet responsibly.

Accessing the dark web safely begins with choosing the right tools. The most common software used is the Tor Browser, which enables users to browse anonymously by routing traffic through a series of encrypted servers. When downloading the Tor Browser, ensure you do so from official sources to avoid malicious versions. It is also recommended to keep your software updated and to avoid revealing personal information while browsing.
To find dark web links, users often rely on directories, forums, and marketplaces that curate lists of onion sites. These sources can provide the latest links, which tend to change frequently to maintain security and privacy. It is crucial to verify the legitimacy of the links before visiting them to reduce exposure to scams or malicious content. Maintaining good security practices, such as using a VPN along with Tor, can add an additional layer of protection.
Dark Web Websites: The Best Onion and Tor Links 2025
As the dark web evolves, new onion sites and Tor links emerge, offering a variety of services and information. Some sites provide forums for discussion, marketplaces for legal goods, or resources for privacy advocacy. However, with the constant rise of illegal activities, it is vital to exercise caution and avoid engaging in or supporting unlawful transactions.
- Use trusted directories and communities that regularly update lists of functioning dark web links to discover reputable sites.
- Verify sites through multiple sources to ensure they are legitimate and safe to visit.
- Employ strong security measures such as a VPN, secure antivirus software, and avoiding downloading files from untrusted sources.
For those seeking dark web links, learning how to differentiate safe sites from dangerous ones is key to a secure experience. Remember, the dark web can offer privacy and anonymity, but it also harbors risks. Always prioritize security and legality when exploring this complex part of the internet.
What is the dark web? How to access it and what youll find
The dark web is a part of the internet that is not indexed by traditional search engines and requires special tools to access. It consists of websites that are hidden behind encrypted networks, often accessed via anonymizing software. While the dark web has legitimate uses such as protecting privacy and enabling free expression in oppressive regimes, it is also known for illegal activities. Navigating this complex underground network requires caution and awareness of risks involved.
To access the dark web safely, users typically rely on specialized software like the Tor Browser, which anonymizes your connection and allows access to “.onion” sites. It is crucial to download software only from official sources to avoid malware or security vulnerabilities. When browsing, avoid providing personal information or engaging in illegal activities. Using a virtual private network (VPN) in conjunction with Tor can add an extra layer of security. Being cautious and well-informed helps reduce exposure to scams, malicious content, and legal issues.
Dark web sites, often known as darknet links, cover a wide array of topics. Some sites offer forums for discussion on privacy, security, and activism. Others may provide marketplaces for goods and services that are not available on the surface web. Many darknet links are hidden and require specific tools to access, but they can sometimes be found through online directories or forums dedicated to dark web navigation. It’s essential to approach these links critically and with the understanding of legal boundaries.
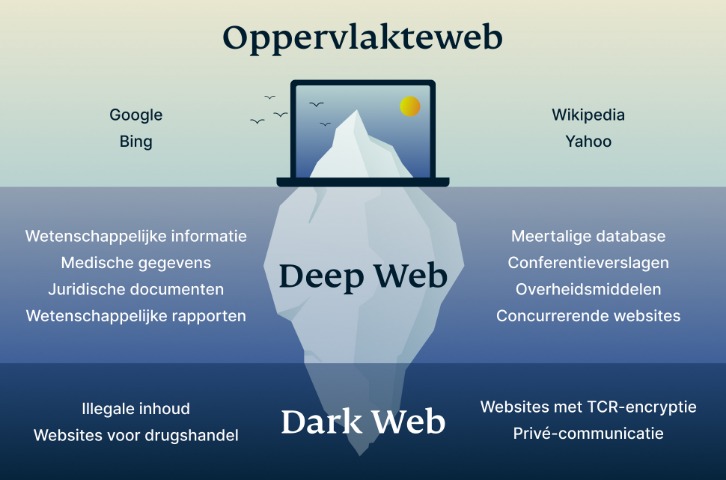
Overall, exploring the dark web can be intriguing and informative, but it should be approached with caution. Proper security measures and understanding of how to access darknet links safely are key to protecting your privacy and avoiding potential dangers. Always prioritize your safety and comply with legal regulations when venturing into this hidden part of the internet.
Dark Directories: Navigating And Gathering Information In The DarkNet OSINT
The dark web is a hidden part of the internet that requires specialized tools and knowledge to access safely. It is often associated with illicit activities, but it also hosts legitimate sites dedicated to privacy, whistleblowing, and secure communication. Navigating the dark web involves careful preparation and awareness of potential risks. Accessing dark web websites securely begins with understanding the importance of using a trusted and updated Tor browser, which anonymizes your traffic and helps protect your identity. Users should always ensure they are on secure networks and avoid providing personal information to avoid compromising their anonymity.

To find dark web links, many users rely on dark web directories and forums that compile updated lists of onion sites. These directories serve as a starting point for exploring various categories like marketplaces, forums, or informational sites. It is crucial to verify the authenticity and safety of links before clicking, as the dark web is rife with scams and malicious content. Employing OSINT (Open Source Intelligence) techniques can also assist in gathering information about specific sites or communities, helping users assess credibility and security. Think of the dark web as a vast network where careful navigation and research are essential for safe exploration.
Dark web links are often shared within specialized communities or through secure channels to maintain anonymity and avoid detection. Some directories organize sites into categories, making it easier to find relevant content. However, caution must always be exercised since malicious actors can create fake or harmful sites to deceive users. Utilizing security tools such as VPNs alongside Tor enhances your privacy and helps mask your location. Overall, accessing the dark web responsibly involves thorough research, cautious link verification, and adherence to safety protocols to ensure a secure browsing experience in the darknet.
How to access the dark web safely
Navigating the dark web safely requires careful preparation and understanding of how to access it securely. The dark web is a part of the internet that isn’t indexed by standard search engines and is accessible only through specialized software. To begin, you’ll need to use a trusted anonymity network such as the Tor browser, which allows you to visit darknet sites without revealing your identity or IP address. Always ensure your device has up-to-date security measures and avoid clicking on unknown links to prevent potential threats. For those interested in exploring darknet links, there are various resources and directories that can guide you to reputable sites. One example of a trusted entry point is this darknet link, which provides access to a curated environment. Remember, accessing the dark web involves risks, so it’s essential to prioritize privacy and security at every step. Staying informed and cautious can help ensure your experience remains safe while exploring this hidden part of the internet.
Dark Web Links A Comprehensive VAPT procedure for Dark Websites
Accessing the dark web can offer a variety of legitimate and secure opportunities for privacy-focused activities, research, or anonymous communication. However, it is essential to approach the dark web with caution and adhere to strict safety protocols to protect your identity and devices from potential threats. The dark web operates on encrypted networks, primarily using Tor (The Onion Router), which anonymizes user activity. To access darknet links safely, users should utilize trusted tools, implement comprehensive security measures, and follow a validated procedure to mitigate risks associated with malicious content and vulnerabilities.
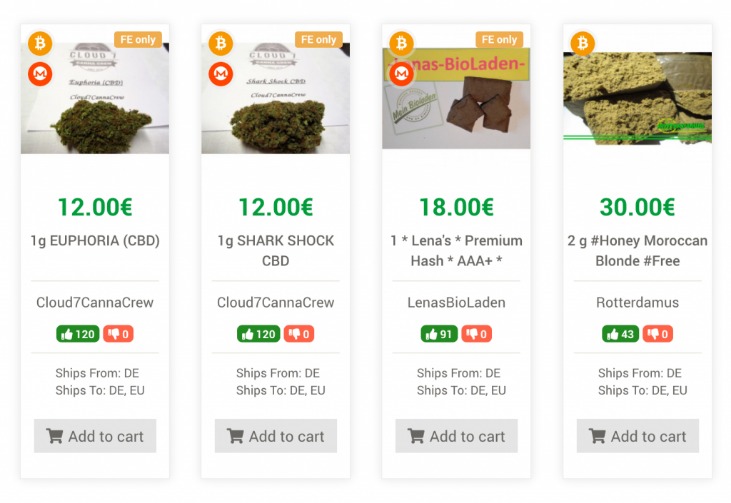
Begin by ensuring your device is secure. Use a dedicated computer or virtual machine that is not linked to your personal identity. Install reputable security software, including antivirus and anti-malware tools, and keep all systems updated with the latest patches. Download the official Tor Browser from an authorized source to guarantee its integrity. When accessing darknet links, avoid clicking on suspicious or unverified URLs, and always verify the authenticity of the sites you visit.
A structured Vulnerability Assessment and Penetration Testing (VAPT) procedure is vital for evaluating the security posture of dark websites or services. This approach involves identifying vulnerabilities within the dark web environment, such as unsafe links, outdated software, or misconfigured servers. Conducting a VAPT involves reconnaissance to discover potential targets, scanning for open ports and service versions, and performing controlled exploits to assess security weaknesses. For darknet links, special care must be taken to avoid exposing the tester to malicious content or triggering security alarms.
Part of a comprehensive dark web security strategy includes deploying secure communication methods, such as end-to-end encrypted messaging, and using VPNs alongside the Tor network to add layers of protection. Establish clear guidelines for handling sensitive information and avoid downloading files or opening unknown attachments. Regularly review and update security protocols based on insights gained from testing procedures to maintain a robust security posture.
It is crucial to remember that browsing or operating on the dark web carries inherent risks, and ethical considerations should always be maintained. By following tested safety protocols, employing systematic VAPT procedures, and using trusted darknet links judiciously, users can minimize potential dangers while exploring the dark web for legitimate and secure purposes.
What is the dark web and how do you access it?
The dark web is a part of the internet that is not indexed by standard search engines and requires specific software to access. It operates on encrypted networks, providing a layer of anonymity for its users. Many people explore the dark web out of curiosity, for privacy concerns, or for secure communication in sensitive situations.
To access the dark web safely, it’s essential to use the right tools and follow security best practices. The most common method is through the use of the Tor browser, which allows users to browse anonymous and access dark web sites known as darknet links. Before connecting, ensure your device has updated security software, and consider using a virtual private network (VPN) to add extra protection and mask your IP address.
When navigating the dark web, be cautious about the links you visit and avoid engaging in any illegal activities. Use reputable sources or directories to find legitimate darknet links, and always verify the authenticity of the sites before interacting with them. Remember that the dark web hosts various content, some of which may be harmful or illegal, so practicing caution is essential for your safety.
- One of the challenges of exploring the dark web is that you can’t just use a search engine and type in what you’re after like you would on the surface web.
- Join me each week, where I’ll break down complex topics and dissect the latest news within the cybersecurity industry and blockchain ecosystem, simplifying the tech world.
- Most e-commerce providers offer some kind of escrow service that keeps customer funds on hold until the product has been delivered.
- The dark web is a hidden part of the internet that requires specialized software to access.
- There are several whistleblower sites, including a dark web version of Wikileaks.
Anonymity Online

Accessing the dark web safely requires understanding the importance of maintaining anonymity and following best security practices. The dark web, a part of the internet not indexed by standard search engines, hosts various sites often accessed via specialized tools and protocols. To explore darknet links securely, you should start by using a reputable privacy-focused browser like Tor, which anonymizes your internet activity and helps protect your identity. Always ensure that your device’s operating system and software are up to date to minimize security vulnerabilities. When visiting darknet links, avoid revealing personal information and be cautious of potential scams or malicious content. Using a trusted Virtual Private Network (VPN) in conjunction with Tor can add an extra layer of protection. Remember that while browsing, it’s essential to disable scripts and avoid downloading files from unknown sources to prevent malware infections. Adopting these practices will help you navigate the dark web more safely, staying anonymous and reducing risks associated with illegal or harmful content.