Darknet Intelligence & Dark Web Data for Cybersecurity Threat Detection
The dark web, often associated with illicit activities, also serves as a valuable resource for cybersecurity professionals seeking to monitor emerging threats and gather intelligence. Darknet websites provide a clandestine environment where cybercriminals communicate, trade stolen data, and orchestrate attacks. By analyzing data from darknet websites, organizations can identify patterns, threat actors, and potential vulnerabilities before they impact their systems. Engaging with darknet intelligence enables proactive defense strategies and enhances overall cybersecurity posture. For those interested in exploring darknet platforms for threat detection, tools and resources are available that facilitate safe and effective monitoring of these hidden networks.
What is the dark web and how do you access it?
The dark web refers to a part of the internet that is not indexed by traditional search engines and requires specialized software or configurations to access. It is often associated with clandestine activities, but also serves as a platform for privacy-focused communications and information sharing. Darknet websites are the specific online locations hosted within this hidden segment of the internet, often using encrypted protocols to maintain anonymity and security for both operators and users.
Accessing the dark web typically requires tools such as the Tor browser, which enables users to navigate through a network of relays that anonymize their IP addresses and location. These browsers connect to darknet websites, which are commonly hosted using “onion” domains, recognized by their unique .onion addresses. Security precautions are essential when exploring the dark web, as it can host both legitimate and malicious content.
In the realm of cybersecurity, the dark web is a critical source of intelligence, providing insights into emerging threats, data breaches, and illicit activities. Monitoring darknet websites can help organizations detect early signs of cyber threats, such as stolen credentials, malware campaigns, and hacker forums. This intelligence enables security teams to respond proactively, mitigate risks, and strengthen defenses against cyberattacks.
True stories from the dark side of the Internet
The darknet represents a hidden layer of the internet where anonymous activities thrive, often remaining inaccessible through standard search engines. These covert websites serve as hubs for various illicit operations, ranging from illegal trading to cybercriminal collaborations. For cybersecurity professionals, gaining insight into darknet activities is critical for detecting and mitigating emerging threats across digital landscapes.
Darknet websites often operate under the cover of anonymity, using specific tools and networks that conceal user identities and locations. This environment fosters a marketplace for stolen data, hacking services, and malicious software, making it a focal point for threat intelligence gathering. Monitoring these sites provides real-time intelligence on new attack vectors, compromised credentials, and trends in cybercriminal operations.
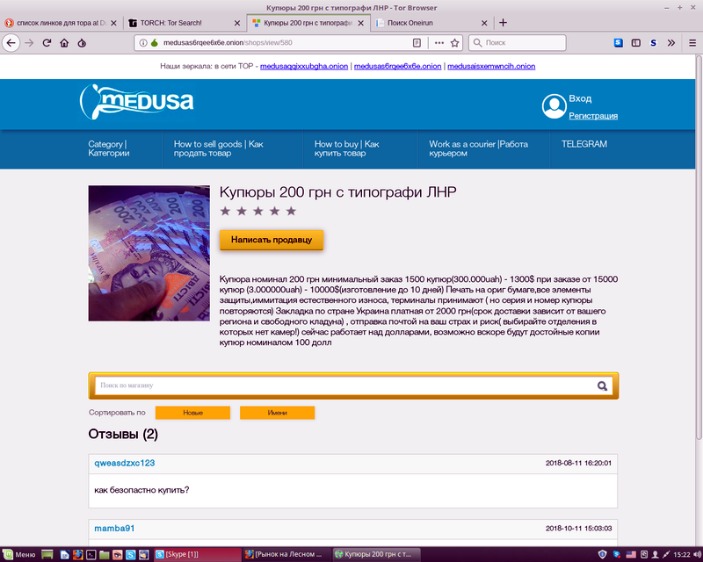
One notable example of darknet intelligence use was when security teams uncovered plans for a large-scale data breach after monitoring a darknet forum. Cybercriminals discussed exploiting a vulnerability in a popular software platform, allowing organizations to patch their defenses proactively before the attack occurred. Such true stories highlight the importance of understanding the dark side of the internet in defending against cyber threats.
Dark web data analysis has enabled cybersecurity experts to track the evolution of cyber threats, revealing patterns that help predict potential attacks. By analyzing communications and transactions on darknet sites, security teams can identify emerging threats, such as ransomware campaigns or targeted phishing schemes. This proactive approach enhances an organization’s ability to prepare and respond effectively to cyber incidents.
In conclusion, darknet intelligence and dark web data are invaluable resources in the modern cybersecurity landscape. They provide actionable insights into cybercriminal activities, helping organizations stay one step ahead of malicious actors by understanding their tools, methods, and intentions. As the dark web continues to be a fertile ground for cyber threats, harnessing this intelligence is essential for comprehensive cybersecurity defense strategies.
The Dark Web Explained: How It Works & Why It’s So Dangerous
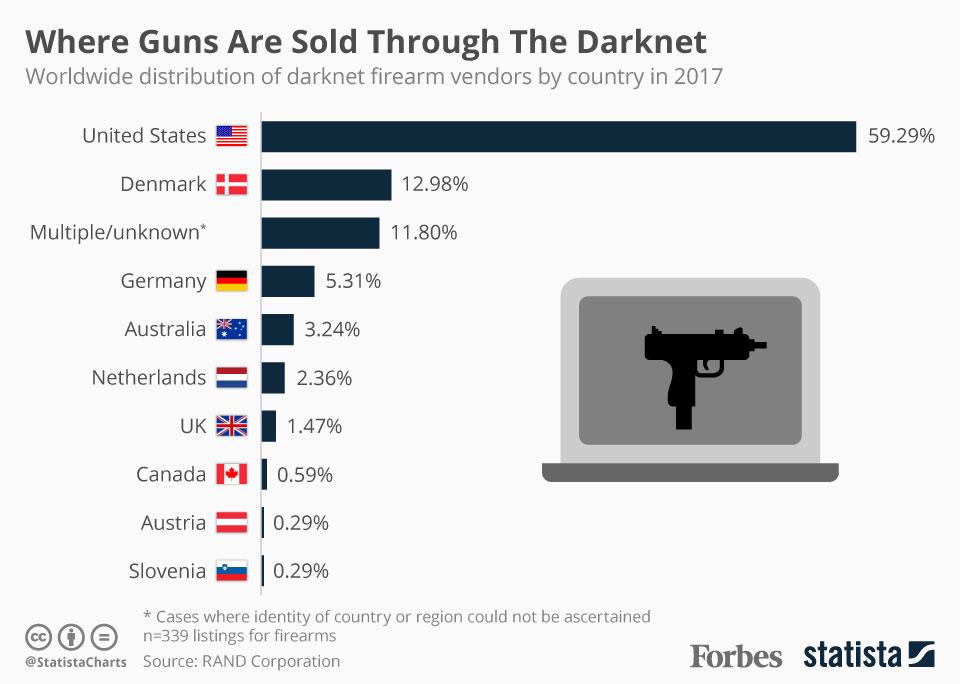
The darknet represents a hidden part of the internet that operates on anonymity and encrypted networks, making it accessible only through specialized software. Unlike surface web pages, darknet websites are not indexed by standard search engines and require specific configurations, such as using the Tor browser, to access. This clandestine environment has gained notoriety for hosting various illegal activities, including illicit markets, hacking forums, and information exchanges, which pose significant challenges for cybersecurity professionals.
Darknet intelligence involves gathering and analyzing data from these concealed networks to identify emerging threats, cybercriminal activities, and potential breaches. By monitoring darknet forums and marketplaces, security teams can detect early signs of planned attacks, stolen data trades, and the dissemination of malware. This proactive approach enhances threat detection capabilities, enabling organizations to respond swiftly to risks before they materialize into actual incidents.
Dark web data plays a crucial role in cybersecurity threat detection, as malicious actors often share hacking tools, exploit kits, and compromised credentials within these hidden communities. The data collected from darknet websites can include leaked personal information, login credentials, and details about ongoing cybercrime campaigns. Analyzing this information allows cybersecurity teams to identify vulnerabilities and prepare defenses against imminent threats.
The dark web is particularly dangerous because of its inherent anonymity and lack of regulation, which facilitates criminal endeavors. The anonymity makes tracing perpetrators difficult, and the wealth of stolen data accelerates cyberattacks across various sectors. Understanding how the dark web functions and leveraging darknet intelligence are essential components of modern cybersecurity strategies, helping organizations stay ahead of sophisticated cyber threats and protecting critical data from falling into the wrong hands.
What Is the Dark Web? How It Works & Why It’s So Dangerous
The dark web is a hidden part of the internet that is not indexed by standard search engines and requires specialized software to access. It operates on a network called the darknet, which provides a layer of anonymity for users and website operators. This anonymity makes the dark web a hub for various activities, both legitimate and illegal, including private communications, whistleblowing, and black market transactions. Darknet websites often host illicit content and services that are inaccessible through conventional browsers, making it a dangerous space for unaware users. Navigating these sites can expose visitors to cyber threats, scams, and legal risks, emphasizing the importance of caution when exploring or considering access to the dark web. For those interested in understanding more about darknet sites, browsing reputable resources and security tips is highly recommended.
Dark Web Hub Searchlight Cyber
The dark web is a hidden part of the internet that is not accessible through traditional search engines or standard web browsers. It exists on encrypted networks that require specialized software and configurations to access, typically using tools like Tor (The Onion Router). This layer of the internet provides anonymity to users and website operators, making it both a secure environment for privacy-focused activities and a hub for illicit activities. Darknet websites are the primary portals within this concealed web, often used for exchanging sensitive information, trading illegal goods, or discussing controversial topics without fear of detection.
How the dark web works involves a complex network of encrypted connections that obscure users’ identities and locations. When accessing darknet websites, users connect through multiple layers of encryption, which route their traffic through various volunteer-operated servers worldwide. This process ensures that neither the user nor the website owner can easily be traced. The anonymity provided by these networks makes the dark web an appealing space for whistleblowers, journalists, and individuals seeking privacy. However, this same feature makes it a hotbed for illegal activities, including drug trafficking, weapons sales, hacking services, and dissemination of illegal content.
The dark web’s notoriety for criminal activities is what makes it particularly dangerous. Cybercriminals frequently exploit darknet websites to conduct illegal transactions away from the watchful eyes of law enforcement. These websites often operate on a decentralized basis, making them difficult to shut down or regulate. Additionally, the anonymity and encryption that protect legitimate users also facilitate scams, hacking, and other cybercrimes. Users should exercise extreme caution when navigating the dark web, as it is a domain where danger can easily lurk behind seemingly anonymous storefronts or discussion forums. Awareness and vigilance are essential to avoid falling victim to scams, malware, or other malicious schemes.
Overall, the dark web remains a complex and shadowy segment of the internet. While it offers privacy and security for legitimate users, its potential for misuse makes it a hazardous environment. Understanding how darknet websites operate helps users appreciate both the benefits and risks associated with this hidden internet realm, emphasizing the importance of cautious and informed navigation to stay safe.
What Are the Best Dark Web Search Engines in 2025?
The dark web is a hidden part of the internet that isn’t indexed by traditional search engines and requires special software to access. It operates as a subset of the deep web, comprising websites that are intentionally concealed from the public eye, often using anonymizing networks like Tor. These sites provide a level of privacy that can be exploited for various purposes, both legitimate and illicit. While some users access the dark web for privacy protection and to communicate securely in oppressive regimes, others use it for illegal activities such as trade of illegal goods, hacking, and other malicious endeavors. The anonymity mechanisms underlying these websites contribute to their danger, making it difficult to track or shut down malicious actors.
How the dark web works involves routing internet traffic through numerous encrypted relays via networks like Tor, which stands for The Onion Router. This process obscures a user’s identity and location, creating a virtually untraceable environment for hosting websites, often called darknet websites. These sites frequently have .onion domain names, accessible only through specialized browsers. Because of this structure, law enforcement agencies find it challenging to monitor illegal activities taking place on the dark web. The relative anonymity and lack of regulation foster an environment where crimes such as drug trafficking, weapons sales, and illegal data exchanges flourish, making the dark web one of the most hazardous parts of the internet to navigate.
As of 2025, some of the most popular dark web search engines include specialized tools designed to index content within the darknet. These search engines help users find relevant darknet websites and marketplaces without having to browse extensively. They typically operate by crawling publicly accessible darknet sites, aggregating data into searchable databases. Because of the volatile and clandestine nature of darknet activities, these search engines are continually evolving and often emphasize privacy and security for their users. Despite their usefulness, users must exercise caution and understand that even with these tools, the dark web remains a dangerous environment with substantial risks associated with illegal content and malicious actors.
10 Tor & dark web links to explore safely in 2025
The dark web is a hidden part of the internet that isn’t accessible through standard search engines or browsers. It operates on encrypted networks, mainly utilizing the Tor network, which allows users to access websites anonymously. The dark web is often associated with illegal activities, but it also serves as a platform for privacy-focused communications and whistleblowing. Due to its anonymous nature, it appeals to those seeking to evade censorship or surveillance. However, this same anonymity makes it a dangerous space filled with illicit markets, hacking forums, and other malicious content.
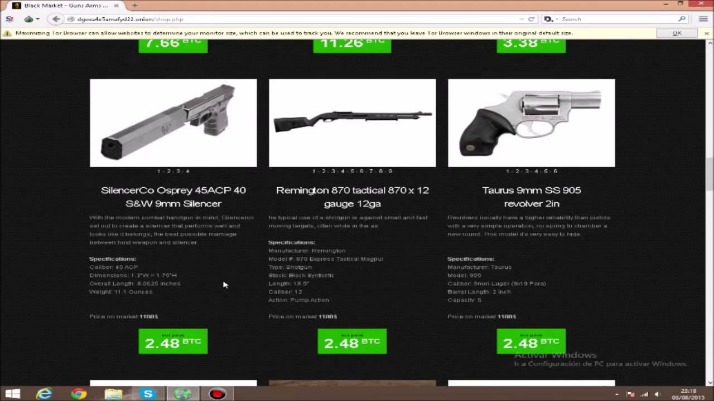
The dark web functions through layered encryption, where users connect via specialized tools like the Tor browser. When navigating dark web marketplaces, forums, or private communication sites, visitors remain anonymous by masking their IP addresses and encrypting their data. This technology enables users to access darknet sites that are not indexed by traditional search engines—these sites often have “.onion” domain suffixes. While some dark web sites are used for legitimate purposes like secure journalism or privacy protection, many are involved in illegal activities such as drug trafficking, hacking services, or stolen data exchanges.
- As a rule, this side of the internet hides content, identities, and locations from third parties that are common throughout the ‘surface web’ (mainstream, public websites).
- Pages on the Deep Web are designed to provide confidentiality, protecting sensitive information from unauthorized parties.
- While it’s generally safe to use, dark web activity can be detected at the entry and exit nodes of the Tor network.
- Unless you know where you’re going, there’s always some risk connected to clicking on dark web search engine links.
- It can only be accessed through special networks like Tor or via static IPs shared privately.
Due to its clandestine nature, the dark web poses significant risks. Users can easily encounter scams, scams, and malicious software. Law enforcement agencies worldwide continuously monitor illegal activities, making the dark web a risky environment for unwary visitors. It is essential to be cautious and avoid engaging in illegal transactions or clicking on suspicious links. To explore darknet sites safely, it’s advisable to use reputable tools, keep security software updated, and never share personal information. For 2025, some darknet websites remain popular and accessible for research or privacy-conscious browsing, but users should always prioritize safety and legality in their online activities.