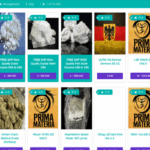
Malware Marketplaces Provide Newcomers with Expanded Capability
Malware marketplaces have revolutionized the cyber threat landscape by providing newcomers with expanded capabilities to acquire malicious tools and services. These platforms serve as hubs where individuals with varying levels of technical expertise can access a wide range of malicious software, including exploits, ransomware, and spyware. The emergence of nexus darknet access has further facilitated this growth, offering a secure environment for traders to exchange illicit digital assets. As these marketplaces evolve, they continue to lower the barriers to entry for cybercriminals, making it easier than ever to engage in malicious activities with minimal technical knowledge. For those interested in exploring secure channels like nexus darknet access, understanding how these platforms operate is essential for grasping the modern dynamics of cybercrime.
Darknet market Wikipedia
- All the analyses indicated in the following were carried out with the open-source R package bibliometrics via the Biblioshiny software.
- However, the Oxen Privacy Tech Foundation (OPTF), which developed the “LokiNet” dark net as well as the end-to-end encryption messenger “Session,” saw an overwhelming influx of Iranian users since September 2022.
- Given the network’s open nature, even the Federal Government is still struggling to control it.
- A source is a journal article published in one or more documents in our bibliographic collection.
Malware marketplaces on the darknet have become significant hubs for cybercriminal activity, providing newcomers with expanded capabilities to access and distribute malicious tools. These marketplaces serve as clandestine platforms where hackers and malicious actors can buy, sell, or trade malware, exploits, and hacking services with relative ease. The emergence of these marketplaces has drastically lowered the barriers to entry for those interested in cybercrime, especially for individuals new to the dark web environment.

One notable aspect of these darknet marketplaces is their role in facilitating the dissemination of various malware types, including ransomware, remote access Trojans (RATs), and trojan horse programs. These marketplaces often feature sophisticated **nexus darknet access** tools, which enable newcomers to quickly and securely connect to hidden forums and transaction sites. Such tools streamline access to the dark web, ensuring that users can navigate safely while engaging in illicit activities.
Darknet marketplaces also operate with a high degree of anonymity, often employing cryptocurrencies for transactions to further conceal identities. This ecosystem creates an environment where inexperienced users can easily acquire malicious software without extensive technical knowledge. This expansion of capabilities demonstrates a concerning trend: the increasing ease with which malicious actors, regardless of experience, can engage in criminal activities online.

In addition to offering malware and hacking services, some darknet markets have evolved into comprehensive platforms that include forums for discussion, tutorials, and shared resources, all accessible through **nexus darknet access** methods. These communities help newcomers learn the basics of cybercrime, further widening the scope of illicit activities and increasing the overall threat landscape.
- Darknet marketplaces offer a wide array of malware and hacking tools accessible to beginners through secure **nexus darknet access**.
- They foster a community environment where inexperienced hackers can learn from advanced cybercriminals.
- The use of encrypted transactions via cryptocurrencies ensures anonymity and safety for participants.
- This environment lowers the barriers to entry into cybercrime, thereby expanding the cybersecurity threat landscape.
Overall, darknet marketplaces powered by **nexus darknet access** represent a growing challenge for cybersecurity professionals, as they facilitate the rapid spread of malicious software and contribute to the proliferation of cyber threats worldwide. The ease of entry and the availability of resources make these marketplaces a focal point for ongoing cybercrime activity and a concern for digital safety.
Top 5 Dark Web Marketplaces to Monitor
Accessing the nexus darknet offers a gateway to a vast and often illicit marketplace environment where malware providers and cybercriminals trade tools, services, and stolen data. These marketplaces have evolved to become sophisticated hubs that provide newcomers with expanded capabilities, allowing malicious actors to acquire or develop malware with relative ease. The nexus darknet access enables users to navigate these hidden channels securely, facilitating transactions and collaborations outside the oversight of traditional cybersecurity measures.

Malware marketplaces on the dark web have proliferated, offering a wide range of malicious software such as ransomware, trojans, and phishing kits. These platforms serve as the backbone for cybercriminal operations, providing a centralized space for buying, selling, or sharing malware strains and hacking services. The accessibility of nexus darknet access simplifies entry into these complex environments, empowering even less experienced actors to participate in cybercrime activities.
Top dark web marketplaces to monitor include forums and platforms that specialize in malware exchanges, exploit kits, and hacking tools. These sites often feature user ratings, escrow services, and detailed listings, making it easier for malicious actors to conduct transactions securely. However, law enforcement agencies and cybersecurity professionals keep a close watch on such marketplaces to track emerging threats and understand evolving attack methods.
Newcomers should exercise caution when delving into these environments, as the nexus darknet access exposes them to significant legal and security risks. These marketplaces often operate under pseudonymous networks, enabling cybercriminals to maintain anonymity. Despite this, understanding the structure and activities of these marketplaces is crucial for cybersecurity defense, as they often serve as the origin points for widespread malware campaigns and data breaches.
In conclusion, malware marketplaces on the dark web exemplify how cybercriminals leverage nexus darknet access to expand their capabilities. Staying informed about these platforms helps security professionals anticipate threats and develop strategies to defend against sophisticated cyber attacks. As these marketplaces continue to grow and evolve, surveillance and research remain essential to mitigate their impact on individual and organizational cybersecurity.
What Lies Ahead For The Nexus Darknet Market
Malware marketplaces have increasingly become a central hub for cybercriminals seeking to acquire sophisticated tools and services. These platforms provide newcomers with expanded capabilities, allowing even those with limited technical expertise to participate in malicious activities. The rise of such marketplaces has significantly lowered the barriers to entry in the cyber underground, making it easier for a broader range of individuals to access and deploy advanced malware, phishing kits, and exploit kits. This democratization of cybercrime tools has led to an escalation in the volume and complexity of cyber threats faced by organizations worldwide.
One notable development in this landscape is the proliferation of the nexus darknet access, which acts as a gateway to hidden marketplaces and forums specializing in cybercriminal activities. The nexus darknet provides a relatively secure environment for vendors and buyers to exchange malicious goods and services with greater anonymity. As a result, cybercriminal operations have become more organized and streamlined, fostering a competitive environment where the latest malware strains and hacking techniques are routinely exchanged and updated.
Looking ahead, the Nexus darknet market is expected to evolve further as cybercriminals adopt more sophisticated methods of obfuscation and encryption to evade law enforcement and cybersecurity measures. Threat actors will likely leverage automation and AI-driven tools to facilitate rapid deployment of malware and conduct large-scale attacks. Moreover, the expanding scope of these marketplaces could enable new types of cyber threats targeting critical infrastructure, financial systems, and personal data. Continuous monitoring and proactive security strategies will be essential for organizations to defend against the expanding capabilities offered by these illicit platforms.

Dark Web Searching
Exploring the dark web can be a complex and intriguing experience, especially for individuals seeking access to hidden networks and specialized resources. Dark Web Searching involves navigating through encrypted and anonymized websites that are not accessible through standard search engines. A key aspect of this exploration is understanding how to safely and effectively access these concealed layers of the internet. For those interested in specialized access points, nexus darknet access provides a gateway to various underground platforms and communities. By utilizing secure tools and understanding the structure of the dark web, users can uncover valuable information while maintaining their privacy and security.
Darknet market and fraud shop BTC revenues decline amid years-long international law enforcement disruption
The nexus darknet access has become a focal point for individuals seeking to explore the hidden corners of the internet, including dark web searching, darknet markets, and online fraud operations. Over recent years, efforts by international law enforcement agencies have significantly disrupted illegal activities on the dark web, leading to a notable decline in revenue generated by illicit shops and marketplaces, especially those handling cryptocurrencies such as Bitcoin. These operations, once thriving hubs for illegal trade, have faced increased scrutiny and shutdowns, causing a shift in the landscape of darknet activities.
Darknet markets traditionally served as platforms for transactions involving drugs, stolen data, and counterfeit goods. However, sustained law enforcement actions have resulted in a decline in their overall activity and revenue. The crackdown has mainly targeted major marketplaces, leading to the closure of many notorious sites and a reduction in the flow of illicit funds, particularly Bitcoin, which was once the preferred cryptocurrency for dark web transactions.
Despite these disruptions, the darknet remains accessible through secured methods like nexus darknet access, enabling users to reach hidden services with increased anonymity. Still, this increased access does not diminish the risks associated with engaging in dark web activities. Law enforcement agencies continue to enhance their capabilities, making it more challenging for fraud shops and illegal vendors to operate profitably.
- The decline in BTC revenues reflects a broader international effort to combat illegal online activities.
- Criminal enterprises are adapting by shifting to alternative cryptocurrencies or more covert operational techniques.
- Law enforcement’s persistent disruption efforts have deterred many from participating in dark web marketplaces.
The ongoing disruption of darknet marketplaces underscores the importance of vigilance and the evolving landscape of cybercrime. As authorities push forward with their investigations and takedowns, the nexus darknet access remains a critical point for researchers, cybersecurity experts, and law enforcement to monitor and understand these illicit networks better. Continued collaboration and technological advancements are vital in preventing the resurgence of illegal activities online.
Nexus Market: Top Darknet Marketplace 2024 Mirrors Link
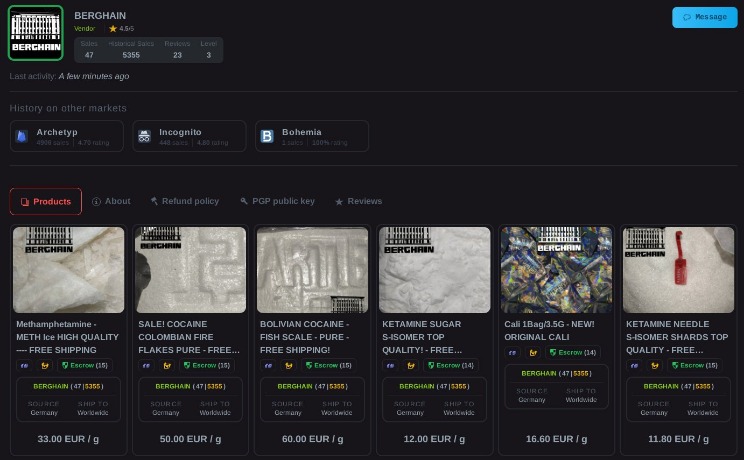
Accessing the dark web, particularly through marketplaces like Nexus Market, has grown in popularity among users seeking privacy and anonymity for various activities. The dark web provides a hidden part of the internet that isn’t accessible through standard browsers, requiring specialized tools such as Tor to enter. Nexus Market has established itself as one of the top darknet marketplaces in 2024, offering a wide range of products and services while maintaining high security standards for its users. Navigating such platforms requires understanding the unique access points and mirror links that ensure continuous availability and access to the site.
To facilitate safe and reliable Nexus darknet access, users often rely on mirror links that replicate the original marketplace. These mirrors help bypass any potential downtime, censorship, or security issues that might affect the primary site. It is crucial to use trusted and verified mirror links to avoid engaging with malicious actors or falling victim to scams prevalent on some darknet platforms. Ensuring a secure connection, updating security measures, and practicing good digital hygiene are essential when exploring darknet marketplaces in 2024.
The dark web market landscape is constantly evolving, with Nexus Market maintaining its position through enhanced security protocols and user trust. For those venturing into the dark web for legitimate purposes, understanding how to access and navigate Nexus darknet safely is vital. Always prioritize privacy, verify links through trusted sources, and remember that engaging with such platforms carries inherent risks. Equipped with the right knowledge, users can explore Nexus Market and similar platforms responsibly while safeguarding their digital presence.
Foundations and trends in the darknet-related criminals in the last 10 years: a systematic literature review and bibliometric analysis Security Journal
The dark web has emerged as a complex and enigmatic segment of the internet, characterized by its anonymous and encrypted nature that facilitates both legitimate and illicit activities. Within this environment, the concept of nexus darknet access has gained significant attention among cybersecurity researchers, law enforcement agencies, and academic scholars. Over the past decade, the dark web has increasingly been exploited by cybercriminals for activities such as illegal marketplaces, illicit financing, and information theft. Understanding the foundational aspects and evolving trends in darknet-related crimes necessitates a systematic review of available literature and bibliometric analysis, shedding light on the patterns and shifts in criminal behavior over time.
Research indicates that the origins of dark web usage in criminal activities can be traced back to early hidden services and anonymous communication platforms. These initial tools provided a haven for whistleblowers, privacy advocates, and, unfortunately, actors engaged in illicit endeavors. As technological advancements enhanced the accessibility and anonymity of darknet platforms, criminal enterprises expanded their operations, leveraging nexus darknet access points to coordinate activities seamlessly across different regions. Recent trends highlight an increase in sophisticated cybercriminal operations, including ransomware campaigns, drug trafficking, and identity fraud, often orchestrated through complex darknet networks.
Bibliometric analyses reveal a growing volume of scholarly work focusing on the darknet’s criminal landscape, emphasizing the importance of understanding criminal networks’ structure and operational tactics. The last decade saw an uptick in studies analyzing the social, technological, and legal dimensions of darknet access. Researchers have identified key patterns such as the rise of cryptocurrency use for transactions, the adoption of privacy-preserving technologies like Tor and I2P, and the emergence of darknet marketplaces that mirror legitimate e-commerce platforms. These developments reflect an evolution toward more organized and resilient criminal ecosystems that utilize nexus darknet access points as critical nodes in their operations.
Emerging trends also suggest a shift toward more covert and decentralized criminal activities, complicating law enforcement efforts. The increased use of encryption and anonymization tools has made it challenging to trace illicit activities and dismantle criminal networks. Conversely, advancements in cyber forensic techniques and predictive analytics are improving detection capabilities. The ongoing research efforts aim to better understand the dependencies and vulnerabilities within darknet access infrastructure, which is essential for developing effective countermeasures against darknet-related crimes.
In summary, the last ten years have witnessed significant developments in the landscape of darknet-based criminal activities, driven by technological innovations and evolving organizational strategies. The concept of nexus darknet access remains central to understanding how these illicit networks operate, coordinate, and expand. Continued scholarly inquiry and bibliometric studies are vital to staying ahead of future trends and strengthening efforts to combat darknet-related criminal activities effectively.